Cybersecurity: Looking beyond the digital perimeter
Now more than ever, criminals, activists, hacktivists, terrorists and state actors are learning to defeat or bypass security measures. Each day, more threat actors are being identified, and their technical acumen is increasing exponentially. While many systems are deployed with appropriate safeguards in place, vulnerabilities develop as technology matures, and these can be exploited to circumnavigate a once-secure system.
I have spent 26 years defending America’s most critical assets in service of both the United States government and military, and have had the privilege of working with a highly talented team of security experts with decades of experience, both in and out of the U.S. Department of Defense. At AECOM, I support both federal and commercial customers to protect them against a wide variety of threats. While my expertise is in wireless security, I work very closely with AECOM cybersecurity experts like Dean Fox, executive vice president for cybersecurity, and physical security experts like Denise Sines, security national practice lead: both incredibly talented individuals, each with more than 30 years of experience.
AECOM has a very unique approach to cybersecurity and risk assessments. We understand that an organization cannot fully assess its cyber vulnerabilities by measuring only its digital perimeter, so we assess and evaluate the interactions between cybersecurity, wireless security and physical security to better understand an enterprise’s true vulnerabilities.
The chart below illustrates AECOM’s approach to enterprise security.
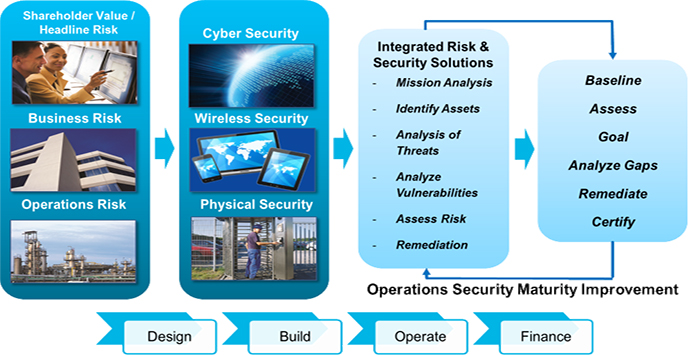
Many modern critical industrial components utilize wireless technologies for communication, so failing to understand the wireless touchpoints in your digital network will prevent you from truly understanding your cyber vulnerabilities. In fact, hackers in two of the most recent notable cybersecurity breaches, Target and Sony, leveraged vulnerabilities in wireless and physical security to access secure digital networks.
There is no one-size-fits-all framework for understanding true threats to your organization, and knowing which control measures provide the best return on investment is not always easy. AECOM’s team leverages diverse expertise to assess and strengthen complex process control, network and computing environments. We integrate cyber and risk strategies into each phase of the development lifecycle to minimize costs while ensuring that the investment secures the lowest-possible risk for the company.
The featured image depicts some of the equipment we operate in support of U.S. Strategic Command. This custom-made vehicle helps us identify critical vulnerabilities within commercial and military command-and-control systems, including cyber and wireless security. The vehicle is ruggedized to allow freedom of movement in all types of terrain — we go where they go!
 Based in Arlington, Va., Ronald Hahn is an executive vice president of AECOM’s enterprise risk analysis program, and an electromagnetic spectrum campaign executive. He has served on the U.S. Department of Defense’s Defense Science Board and has written several articles on the convergence of cybersecurity and the electromagnetic spectrum, which have been published in the Journal of Electronic Defense and the Marine Corps Gazette. His hobbies include golf, scuba diving and riding his Harley Davidson motorcycle.
Based in Arlington, Va., Ronald Hahn is an executive vice president of AECOM’s enterprise risk analysis program, and an electromagnetic spectrum campaign executive. He has served on the U.S. Department of Defense’s Defense Science Board and has written several articles on the convergence of cybersecurity and the electromagnetic spectrum, which have been published in the Journal of Electronic Defense and the Marine Corps Gazette. His hobbies include golf, scuba diving and riding his Harley Davidson motorcycle.
LinkedIn: Ronald Hahn







